Qt-SESAM
SESAM — Super Easy & Secure Authentication Management
Qt-SESAM generates and manages passwords — safely, securely, and for free.
With Qt-SESAM you can generate and manage passwords for any service, e.g. websites, accounts, or apps. The passwords are generated in real-time from your master password and some service specific settings. That means that even in the almost impossible case someone managed to decrypt your encrypted settings he'd still doesn't know your master password and therefore won't be able to login to any of the services. For services which don't allow passwords to be changed (e.g. credit cards) Qt-SESAM can also store fixed (a.k.a. legacy) passwords.
You can share Qt-SESAM's settings across your computers via a dedicated synchronization server and/or a file located on a cloud drive like OwnCloud, Dropbox, Google Drive, or Microsoft OneDrive. This is secure because all of your settings are AES-encrypted with a 256 bit key.
Qt-SESAM runs on Windows, Linux, and Mac OS X. An Android app compatible to Qt-SESAM is underway.
Get Qt-SESAM
- Binaries are available for Windows and Mac OS X
- Linux users have to compile Qt-SESAM from the source code. Help is wanted to build packages for Debian.
Here we go
On first start Qt-SESAM asks for your master password. Without that secret neither passwords can be generated, nor decryption keys be calculated. Because the encryption methods used (AES in CBC mode with a 256 bit key) are known to be secure, the overall security of the application and your data solely depends on the security of the master password. So choose is wisely: not too hard to remember, but long enough nobody else can guess it. And keep it in a safe place! A master password of at least 10 characters is recommended. To make sure you've entered the master password correctly you've got to enter it twice:
While you type, the dialog tells you how strong the chosen master password is.
Ratings range from useless
over you can do better
, mediocre
, good
, very good
, and fabulous
to supercalifragilisticexpialidocious
.
The OK button is activated only after you've entered the same master password again.
Sync first!
The first time you start Qt-SESAM on a certain computer it asks you about whether or not you like to provide information about your synchronization facilities. If this is the first time you ever used Qt-SESAM or don't want to synchronize your settings across computers, you can ignore the advice. In any other case you're taken to the Options dialog where you can select a file to synchronize with, or the hostname of synchronization server (see figures below).
If you acted against your better judgement, be prepared to run into problems while using Qt-SESAM. This is because when starting Qt-SESAM for the first time on a computer, the application generates the so-called key generation key (KGK). The KGK is used to derive your passwords later on. Given that all other settings are the same, different KGKs lead to to different passwords. Getting your settings, which include the KGK, from a synchronization file or server beforehand effectively prevents problems with diverse KGKs.
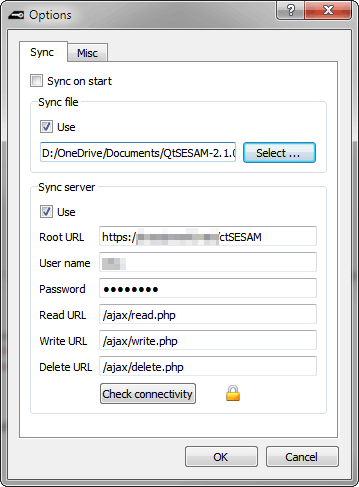
Set your synchronization settings in Options/Sync. You can both synchronize with a file or a server. The file should reside on a cloud drive.
How to set up the server is described in the c't SESAM Server wiki. Click on Check connectivity when you're finished with configuring the synchronization server.
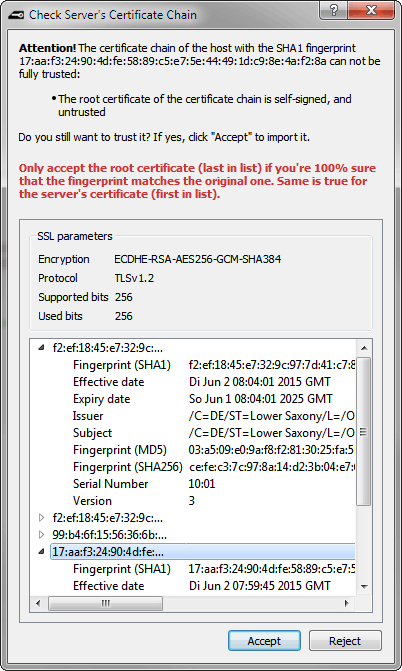
If your configuration was correct, Qt-SESAM displays the server's certificate chain. Please check that the certificate chain actually is the one you've configured on the server. This is easily done be comparing the fingerprints. If the received ones match the configured ones, you can Accept the chain.
Qt-SESAM will then try to read your settings from the server. On success a tiny padlock is displayed next to the Check connectivity button in Options/Sync.
First steps
Enter a new domain by typing its name into the combo box. You'll notice that the generated password changes while you type. That's because the algorithm for password generation weaves the domain name into the eventually generated password. The same is true for the user name.
Unique and Easy
Most of time the default settings for password generation will suffice (16 characters: digits, lowercase and uppercase). If you need more control over how the password is being generated, try out Qt-SESAM's unique feature: the easy selection widget. It lets you choose the complexity and length of the password with a single click. Red indicates bad passwords, green good ones. Move the marker horizontally to change password length, and vertically to change the set of characters the password is composed of. A set for digits as well as for lowercase and uppercase characters is predefined. You can define your own set by typing it into the field below the easy selection widget which is prefilled with some special characters:
Very neat: the widget tells you how long the Tianhe-2 supercomputer and your computer would need to crack a password with the selected settings. As you can see, increasing the password length lets the strength grow much faster than increasing the number of characters in the set. That's because the length flows in exponentially.
Internals
Basics
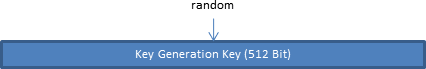
Key Generation Key
The crucial element of the Qt-SESAM's encryption/decryption/generation processes is the key generation key (KGK). The KGK is a 512 bit value randomly chosen the first time you start Qt-SESAM on your computer. It's used to derive the generated passwords and to generate a key to encrypt and decrypt the program settings.
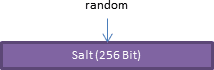
Salt
The salt is also random data. It's used to protect the generated passwords and cryptographic keys against dictionary attacks and rainbow table attacks. More on that later.
Key computation
Any time Qt-SESAM saves the settings to a file or transfers them over the net to the synchronization server the settings are encrypted with AES in CBC mode. Qt-SESAM uses the strongest possible AES encryption with a 256 bit key.
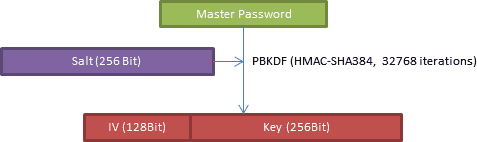
Like any symmetric cipher AES employs a key to encrypt or decrypt data. At the beginning of an encryption or decryption process AES has to be initialized with a block of 128 bit. This initialization vector (IV) is computed along with the key from your master password through a process called key derivation. A well-tested manifestation is the Password-Based Key Derivation Function 2 (PBKDF2) which scrambles your master password with the salt just generated. It does this by repeatedly (32768 times) running the inputs through a hash-based message authentication code (HMAC).
The repeated hashing adds a lot of computational work to derive the key from the password. That makes it especially hard for an attacker to find the password for a known hash by brute-force methods. The HMAC used by Qt-SESAM utilizes the hashing algorithm SHA-384 because it provides a 384 bit result needed to yield the 256 bit AES key and 128 bit IV.
Password generation
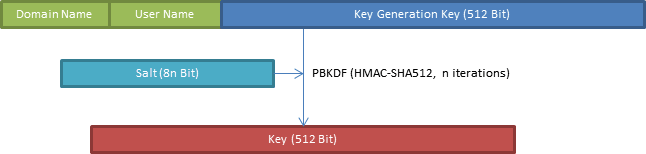
A similar method comes into effect when generating a password. First, the KGK is appended to the domain and user name to form the input to PBKDF2, spiced with a salt.
The salt is shuffled the moment you create the entry for the domain or renew the generated password by pressing the button left to the password field. You can set the length of the salt via Options/Misc/Salt length. The default (and reasonable) length is 16 byte. More than 64 byte are pointless.
You can determine the number of iterations by selecting the value in the corresponding spinbox (first expand the Advanced settings section). The default value can be set via Options/Misc/Default PBKDF2 iterations. The higher the iteration count, the better. Higher values lead to longer to computation times which in turn can make the user interface somewhat doughy. The default value of 8192 is sufficient. For instance, the Wi-Fi security protocol WPA2 uses 4096 iterations.
The result of the operation is a 512 bit key
. Eventually, the password is calculated from this value (see Password::mix()).
Encryption
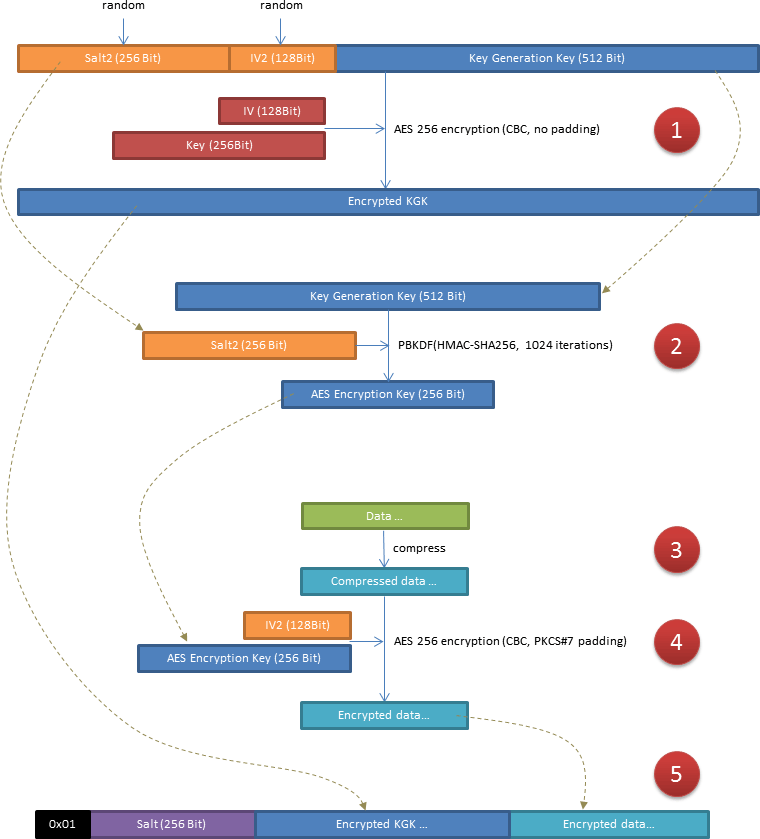
Qt-SESAM's encryption process looks very complicated but in fact is quite straightforward (see figure below):
-
Because Qt-SESAM requires the KGK to generate your service passwords, the KGK has to be stored together with the domain settings.
And because the KGK is needed to encrypt/decrypt the domain settings, it has to be encrypted separately.
A second pair of salt and IV is generated for later use, and prepended to the KGK.
The encryption process applies the key and IV returned by
Crypter::makeKeyAndIVFromPassword()in the previous steps. This means that the data is effectively encrypted with your master password. - The freshly generated salt from step 1 is used to protect the AES encryption key (1024 times spun through PBKDF2) against dictionary and rainbow-table attacks.
- The domain settings are formatted in JSON. This is a rather verbose format for data representation and is easily compressed to a fraction of its original size. But compression does not only save space, it also adds computational effort for an adversary who has seized the encrypted data and tries to decrypt it by brute force.
- The key from step 2 together with the IV shuffled for step 1 is used to encrypt the domain settings after they've been compressed.
-
Now the encrypted data can be assembled: The first byte is a version flag (currently only
0x01is used). Thereon follows the salt that was used to make the key and IV from the master password, then the encrypted KGK from step 1, and the result of step 4. This package can be stored anywhere without the fear of being compromised even if the hacker had long-term access to supercomputers. The privacy of the data contained therein totally relies on the strength of the master password — and how well you hide the password from prying eyes.
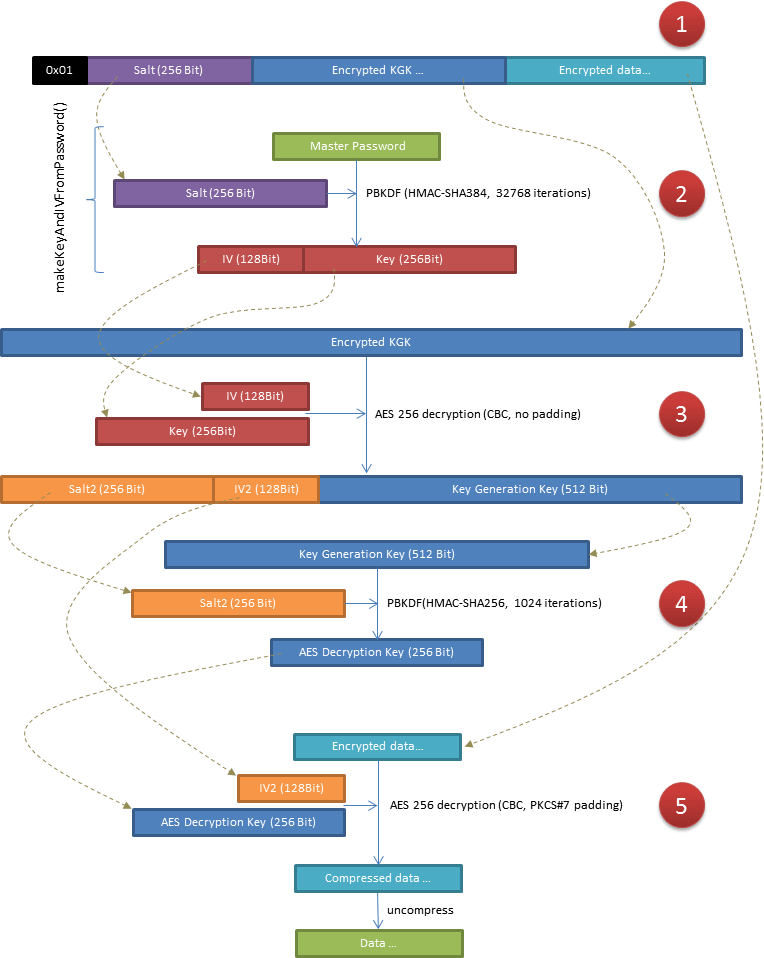
Decryption
Decrypting data works the other way round. Only the master password must be input for decryption. All the other intermediately needed secrets and other bits of data are extracted piece by piece:
- After checking that the version number is
0x01the encrypted package is deconstructed into its three parts. - The master password together with the extracted salt gives the key and IV needed to …
- … decrypt the encrypted KGK, salt, and IV.
- Now that the salt is available it can be used to calculate the decryption key.
- The encrypted data can then be decrypted with that key and the IV from step 3. After deflation the data is ready for use.
Important infos
- FAQ in German
- Build instructions for Linux
- Build instructions for Windows
- How to contribute to Qt-SESAM
Further reading
In German:
- Johannes Merkert, Fensterbeschwörung, PySide: grafische Programme mit Python und Qt, c't 1/16, S. 178
- Oliver Lau, Sesam, synce dich!, Den c't-SESAM-Synchronisierungsserver installieren, c't 23/15, S. 182
- Johannes Merkert, Passwort-Erinnerer, Programmieren lernen mit Python, Teil 2, c't 21/15, S. 158
- Oliver Lau, Sesam, öffne dich!, Passwörter verwalten mit c't SESAM, c't 20/15, S. 182
- Johannes Merkert, Schlangenbeschwörung für Einsteiger, Programmieren lernen mit Python, c't 18/15, S. 118
- Oliver Lau, Aus kurz wird lang, Passwörter sicher speichern mit Hilfe von PBKDF2, c't 17/15, S. 180
- Jürgen Schmidt, Eines für alle, Ein neues Konzept für den Umgang mit Passwörtern, c't 18/14, S. 82